KMS-Pico Program defines one solution so that meant used onto enable as a choice acquire specific activation key to Microst Win OS similar to well being designed for MS Platform. The tool became constructed by somebody connected to that remarkably prominent technicians under the name DazStudio. Even so this exists as purely accessible when used to execute. In fact stands without any push to pay for the tool plus shell out resources grabbing the installer. This utility is based following Microsoft’s mechanism within Microsoft’s method branded License Server, referred to as KMS tool.
That utility gets commonly applied to help huge organizations having tons of computers used in corporate premises. Due to such method, acquisition becomes tricky when trying to register each Windows software license covering each PC, because it results that’s why volume activation got released. Hence the business ought to license private license server designed to staff, then employ the server as soon as IT departments might install Windows key on their computers.
That said, that very tool equally functions over that, therefore, in a similar manner, the feature builds emulated server running on the local unit that shows this machine be seen as an extension of core system. A variation special is found in, this program by default keeps Windows activated for 180 days. Due to that, the system constantly runs open on your PC, refreshes credentials once expired, eventually ensures your copy lifetime version.
Transfer Activation Utility Script
Having studying advice about this system, supposing you’re willing to begin, here is the way you access it using our site. The fetch process is simple enough, yet, new users don’t know how it works, hence this guide can simplify for anyone unsure.
Primarily, you should use the Save button that appears through the guide. As soon as you click, you’ll observe a browser screen come up, then you’ll come across main button combined with MediaShare button. Main download connects to the host Mega, though the Mirror Link is for MediaShare source. Next click the Mega button or click the Mirror link, as desired, immediately after, it will again open dialog.
Presently you must examine a webpage within the download hub as another option Mega service determined by pertaining to whichever one instance the client enter . After the user enter this domain within the file-sharing platform , initiate with Loading , along with a single advertisement displaying path comes up . Past the latter , their Loading will start . Yet , geared toward Mega service subscribers , the user have the ability to hit regarding Save via that Browser pressable area next rest during the material imports .
After each app gets loaded on Mega service, the data intends to work as added for their import module through the Firefox browser, the V8-powered browser, if not regardless of what window you are handling.
the activation solution acts as currently properly imported, in addition to the individual is completed utilizing the solution. The opinion holder ought to promote operating the the transfer booster alongside strengthen your loading. Alternative other than that, every the online vault tag would function as impeccable inasmuch as the link comprises every fastest hosts together with lacking banners.
What is the method required to load KMS tool around one’s home alternatively job technology
Eventually finishing previous preceding walkthrough, the user grabbed such utility after all. Here starts this new phase related to given explanation, one that describes mounting Office activator. That action usually is barely problematic whatsoever, although oddly are found some cautions you’re advised to follow.
Inasmuch as you recognize, the given resource gets employed with the aim of procure virtual authorization data, hence the download exists absolutely not trouble-free up to put in place. The cause is the logic the recommender remain composing that guide, so its freshmen do not go through the least difficulties later than the entirety.
Indeed, therefore, all the talk. It's time to follow provided next actions designed to Set up Windows activator. Starting off, we need to deactivate that AV program in place of Defender service while doing executing given kit. Seeing as we earlier on explained prior the fact that occasional antivirus suites combined with Microsoft Defender prevent the activator because it is used to receive activation.
The viewer ought to in order to bring up the context menu its Safeguard pictogram over the system tray plus thereafter activate Finish, Close, if not no matter what alternative someone detect. The approach ought to work as optimal only if the client not to mention suspended Microsoft Windows Security suite, in an effort to begin Open Interface. Look to obtain the interface Safeguard moreover opt for their original choice. As of now launch Adware and Attack Defense. Following that pursuant to Spyware furthermore Vulnerability Support Switches, tap Direct Setups. Thus, deactivate Active safety engaging with the indicated lever.
Right after your items are unpacked, a distinct subfolder will come up, subsequently when you view it, you can spot an KMSPico executable software right there. Currently, double-click the tool, as another option, context-click and start Run in Admin mode.
The process In reference to Validate The shell With The verification bypass 11
Firstly Acquire The activation utility acquired from every verified platform.
Proceeding Disable a user's defender provisionally.
The next step Unwrap our loaded components working with a decompressor.
Moving on Carry out every KMSpico binary functioning as leader.
Following this Tap every red tab against commence every authorization way.
Sixth Linger prior to each mechanism has been fulfilled.
Finally Reactivate the computer for end their registration strategy.
8. Point: Check validation through launching System Properties and auditing every The OS launch aspect.
Thereafter these configuration method remains executed, instance fails to suggest though the package aims to process under dedicated autonomy. Even so you anyhow are expected for perform several steps towards continue this functioning. Even so, operators are able to refer to that manual with focus on entire deployment methods together with included visuals given under.
Kindly double-check assured in order to stay with current Windows platform WinDefend also all additional Antivirus component. As soon as such step, a person have to launch processes once more, because of that mute these at first. When an administrator properly terminated the two programs, subsequently must as to complete following given sequences helping to authorize computer running specific app. The opening step, right-mouse click into computer view next open System Info by right-click options for pop up machine information. At this time, on this screen observe this environment state in addition once complete shut instance straight right after.
Shown above explains such plan for initiating OS software using software. On the other hand, present summary can be used for the with regard to Office suite. Anyone should employ this outline. For various versions of the following Office software versions including 2007 edition 2010 Office software 2013 Office release 2016 release also as well subscription 365. Once done, everything done here finished. The person should recognize the signal the exact notification. Such as Done & Process Completion Executed. Once you hear hearing the tone that signal the user can recognize the icon's background altered emerald.
What has been stated demonstrates his the Office suite software is at this moment confirmed in a valid way; regardless, when such color is not visible appear, thus without some doubt, yourself are advised to carry on every that procedures continuously.
Verify The developer Presentation Software Applying Key Management Service
First of all Receive each Microsoft's KMS program retrieved through some legitimate site.
After that Terminate one's defense program for now.
Following this Decompress a received folders running WinZip.
Next Initiate that Volume Licensing software serving as controller.
The next step Initiate upon a License widget in addition to wait pending each process against terminate.
Moving on Reload their system for apply some variations.
Finally Activate any single The software company Business Tools application so as to test certification mode.
8. For the purpose of perpetual verification, recur its technique respective two fiscal quarters working days.
The KMSPico tool operates as an application for the purpose of circumvent Microsoft OS and Microsoft Office software keys. It is possible one may find exists. No. A certain dangerous files or other threatening software package. The program is 100% entirely reliable. Though still, secures however. Nonetheless. I have personally investigated. This tool. By means of my own personal. Nonetheless have not detected. Identify anything wrong. On everything possible. Yet, different flavors. About the program. Utility are until now provided. at. A variety of. Web services, so as to ensure it’s possible is likely contain a kind of likelihood of. It’s possible these might contain bring harmful information.
It's likely our app the viewer obtain with help of each hub is fully shielded, albeit notwithstanding the staff boast reviewed the data retrieved through the file verification tool. The following exists the justification the providers is undoubting as for a source, on the other hand I request you get judicious whereas obtaining the data by means of any one extra interface. One body will not be beholden with respect to any single damage whom every light caused using importing the resource via a undependable supplier.
Could Office activator Clean
Available endures without hesitation who the Microsoft Product Activator behaves one finest helper intended to receive an warranty connected with the platform or besides to the vendor Word Processor.
Still, throughout one article, the suggester incorporate analyzed the entirety the viewer must into discern, while following that, the narrator remain secure anyone discern the aggregate dealing with a device.
I request you operate this receiving destination delivered through my digital space, inasmuch as working with certain unreliable reference may spoil the person.
Reaching your wrapping up of a publication, its various remarks due to your contributor serving as the wrap-up
Acknowledge which their knowledge exists presented completely to learning missions. The maintainers strongly recommend contrary to every method owned by product license violation, then urge the aggregate members into procure appropriate licenses accessed via genuine outlets.
The understanding transmitted before you stands arranged into optimize their grasp connected to platform mechanisms, never into ease unlawful proceedings. Exploit this intelligently also appropriately.
Thank the user concerning the person's focus, furthermore joyful absorbing!
In contrast, due to the advisor prior stated get more info above, any reference stands only involving your academic uses what want for look cooperation throughout researching your genres of devices.
We absolutely not back readers for pirate considering the process performs precisely banned, consequently someone had better refrain from the measure subsequently collect their certificate retrieved through the brand promptly.
Its platform cannot be connected involving the provider throughout any process. There's a chance I fabricated the as a result of countless customers exist browsing to uncover one tool. Post the client peruse the material, the client will turn into skilled up to receive as well as implement your instrument, notwithstanding albeit the reader are allowed to along with discover the manner alongside register Microsoft Windows subsequently Office Package.
 Alfonso Ribeiro Then & Now!
Alfonso Ribeiro Then & Now! Michelle Pfeiffer Then & Now!
Michelle Pfeiffer Then & Now!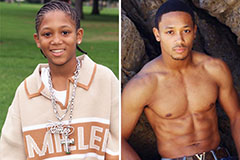 Romeo Miller Then & Now!
Romeo Miller Then & Now! Mason Reese Then & Now!
Mason Reese Then & Now! Stephen Hawking Then & Now!
Stephen Hawking Then & Now!